Configuring PPP Authentication # Method1
By configuring authentication on our serial interfaces, we can restrict access to our router. This is not just useful, but it is highly recommended to implement authentication and a high level of security on all devices whenever possible, especially the ones facing the Internet.
required steps
Configuring a basic authentication is very simple. All you need to do is to create a user account on each router using the other routers hostname as username and a common password, and instruct the router to use some form of authentication (PAP, CHAP, MS-CHAP, …) on the serial interface.
The passwords MUST match on both routers otherwise the authentication is going to fail!
Also, you need to change the encapsulation mode to PPP if you didn’t specify it when you set up the serial connection.
optional commands
The passwords which are associated with usernames are stored in clear text in the configuration. You could use the service password-encryption command to apply a light encryption on all clear text passwords.
before you begin
You should have a working serial connection configured already. You can go through quickly the Configuring Serial Interfaces tutorial and come back here once it’s up and working. It is always good practice to issue a few debug commands related to the configuration you are just about to make so you see the changes immediately. You could use debug ppp authentication or debug ppp negotiation commands.
configuration
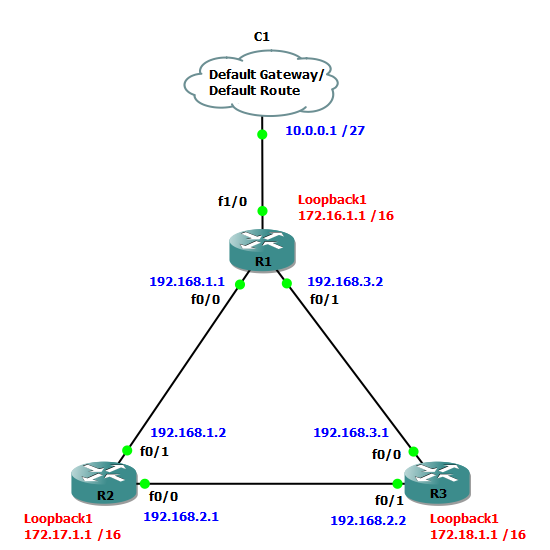
Let’s start on R1. First check if the connection is up and working with a ping.
R1
R1#ping 192.168.1.2 Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to 192.168.1.2, timeout is 2 seconds: !!!!! Success rate is 100 percent (5/5), round-trip min/avg/max = 16/16/16 ms
Let’s enable debugging and the encryption of clear text passwords.
R1#debug ppp authentication PPP authentication debugging is on R1#conf terminal Enter configuration commands, one per line. End with CNTL/Z. R1(config)#service password-encryption R1(config)#
Create a user called R2 and change the encapsulation type to PPP
R1(config)#username R2 password C1sc0
R1(config)#interface serial0/0
R1(config-if)#encapsulation ppp
*Mar 1 11:30:50.099: Se0/0 PPP: Using default call direction
*Mar 1 11:30:50.103: Se0/0 PPP: Treating connection as a dedicated line
*Mar 1 11:30:50.103: Se0/0 PPP: Session handle[7C000008] Session id[0]
*Mar 1 11:30:50.103: Se0/0 PPP: Authorization required
*Mar 1 11:30:53.104: %LINEPROTO-5-UPDOWN: Line protocol on Interface Serial0/0, changed state to down
At this point the line protocol goes down due to encapsulation mismatch! It will come back again as soon as we configure R2 as well.
Enable authentication on the interface
R1(config-if)#ppp authentication ? chap Challenge Handshake Authentication Protocol (CHAP) eap Extensible Authentication Protocol (EAP) ms-chap Microsoft Challenge Handshake Authentication Protocol (MS-CHAP) ms-chap-v2 Microsoft CHAP Version 2 (MS-CHAP-V2) pap Password Authentication Protocol (PAP) R1(config-if)#ppp authentication chap
Now move on to R2 and do the same. Remember when creating a user account you need to use R1 as the username!
R2
R2#debug ppp authentication PPP protocol negotiation debugging is on R2#conf terminal Enter configuration commands, one per line. End with CNTL/Z. R2(config)#service password-encryption R2(config)#username R1 password C1sc0 R2(config)#interface serial0/0 R2(config-if)#encapsulation ppp R2(config-if)# *Mar 1 16:21:50.611: Se0/0 PPP: Using default call direction *Mar 1 16:21:50.611: Se0/0 PPP: Treating connection as a dedicated line *Mar 1 16:21:50.611: Se0/0 PPP: Session handle[39000007] Session id[0] *Mar 1 16:21:50.611: Se0/0 PPP: Authorization required *Mar 1 16:21:50.619: Se0/0 PPP: No authorization without authentication *Mar 1 16:21:50.623: Se0/0 CHAP: I CHALLENGE id 1 len 23 from "R1" *Mar 1 16:21:50.631: Se0/0 CHAP: Using hostname from unknown source *Mar 1 16:21:50.631: Se0/0 CHAP: Using password from AAA *Mar 1 16:21:50.631: Se0/0 CHAP: O RESPONSE id 1 len 23 from "R2" *Mar 1 16:21:50.651: Se0/0 CHAP: I SUCCESS id 1 len 4 *Mar 1 16:21:53.608: %LINEPROTO-5-UPDOWN: Line protocol on Interface Serial0/0, changed state to up R2(config-if)#ppp authentication chap R2(config-if)# *Mar 1 16:22:16.301: Se0/0 PPP: Authorization required *Mar 1 16:22:16.313: Se0/0 CHAP: O CHALLENGE id 1 len 23 from "R2" *Mar 1 16:22:16.317: Se0/0 CHAP: I CHALLENGE id 2 len 23 from "R1" *Mar 1 16:22:16.321: Se0/0 CHAP: Using hostname from unknown source *Mar 1 16:22:16.325: Se0/0 CHAP: Using password from AAA *Mar 1 16:22:16.325: Se0/0 CHAP: O RESPONSE id 2 len 23 from "R2" *Mar 1 16:22:16.325: Se0/0 CHAP: I RESPONSE id 1 len 23 from "R1" *Mar 1 16:22:16.329: Se0/0 PPP: Sent CHAP LOGIN Request *Mar 1 16:22:16.333: Se0/0 PPP: Received LOGIN Response PASS *Mar 1 16:22:16.337: Se0/0 PPP: Sent LCP AUTHOR Request *Mar 1 16:22:16.341: Se0/0 PPP: Sent IPCP AUTHOR Request *Mar 1 16:22:16.345: Se0/0 CHAP: I SUCCESS id 2 len 4 *Mar 1 16:22:16.345: Se0/0 LCP: Received AAA AUTHOR Response PASS *Mar 1 16:22:16.349: Se0/0 IPCP: Received AAA AUTHOR Response PASS *Mar 1 16:22:16.349: Se0/0 CHAP: O SUCCESS id 1 len 4 *Mar 1 16:22:16.353: Se0/0 PPP: Sent CDPCP AUTHOR Request *Mar 1 16:22:16.357: Se0/0 PPP: Sent IPCP AUTHOR Request *Mar 1 16:22:16.361: Se0/0 CDPCP: Received AAA AUTHOR Response PASS
At this point the connection is fully restored, all debugging should stop and ping should succeed. Let’s see!
R2#ping 192.168.1.1 Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to 192.168.1.1, timeout is 2 seconds: !!!!! Success rate is 100 percent (5/5), round-trip min/avg/max = 16/16/20 ms R2#
verification
The debug output is usually enough and the ping worked too, so all that is left to check is the password encryption.
R1#show run | section username username R2 password 7 123A5404115B R1#
The section output modifier requires IOS version 12.3(2)T or higher!
The original password C1sc0 became 123A5404115B.
You can also check the encapsulation using the show interface s0/0.
R1#show interface s0/0
Serial0/0 is up, line protocol is up
Hardware is PowerQUICC Serial
Description: LINK TO R2
Internet address is 192.168.1.1/30
MTU 1500 bytes, BW 1544 Kbit, DLY 20000 usec,
reliability 255/255, txload 1/255, rxload 1/255
Encapsulation PPP, LCP Open
Open: IPCP, CDPCP, loopback not set
Keepalive set (10 sec)
Last input 00:00:34, output 00:00:05, output hang never
Last clearing of "show interface" counters 00:57:07
Input queue: 0/75/0/0 (size/max/drops/flushes); Total output drops: 0
Queueing strategy: fifo
Output queue: 0/40 (size/max)
5 minute input rate 0 bits/sec, 0 packets/sec
5 minute output rate 0 bits/sec, 0 packets/sec
642 packets input, 24629 bytes, 0 no buffer
Received 0 broadcasts, 0 runts, 0 giants, 0 throttles
30 input errors, 0 CRC, 30 frame, 0 overrun, 0 ignored, 0 abort
738 packets output, 26262 bytes, 0 underruns
0 output errors, 0 collisions, 52 interface resets
0 output buffer failures, 0 output buffers swapped out
70 carrier transitions
--More--
Check the authentication method.
R1#show run | section interface Serial0/0
interface Serial0/0
description LINK TO R2
ip address 192.168.1.1 255.255.255.252
encapsulation ppp
no fair-queue
ppp authentication chap
R1#
This type of authentication works fine as long as you don’t change the hostname on the routers! As soon as you change it, the router(s) will try to negotiate with their NEW hostname as username(s). Because the other router doesn’t know the new name, authentication will fail and the interfaces go down! There is a way of avoiding this by specifying a username to use for authentication. To find out how to configure this, read the tutorial Configuring PPP Authentication # Method2.
commands explained
Commands used with a brief explanation.
debug ppp authentication: Enables debugging of ppp authentication
service password-encryption: Applies a light encryption of all clear text passwords stored in the configuration. Passwords added later will also be encrypted
username R2 password C1sc0: Creates a user called R2 with a password C1sc0
encapsulation ppp: Changes the encapsulation mode to PPP. On Cisco routers the default is HDLC
ppp authentication chap: Sets CHAP as the encapsulation method
show run | section username: Shows the section beginning with username from the configuration
show interface s0/0: Shows detailed information about the interface
show run | section interface Serial0/0: Shows the relevant section of the running configuration
I tried this method, but i have a problem…
the command “debug ppp authentication” and “service password-encryption” dont work… by the way, im using boson net sim v5 beta…
When you say that “debug ppp authentication” doesn’t work do you mean that there is no output or the router doesn’t accept it? The “service password-encryption” might be missing from the Boson net sim. I can’t say for sure, I’ve never used it. Although their exams for Cisco are really good! Harder than the real exam!
the error that comes is:
% Invalid input detected at ‘^’ marker
and ‘^’ is pointing to authentication….
i “typed debug ppp ?” and the only option available is negotiation… Any help? btw, im doing basic ccna at the institute im studying at…
It looks like that the simulator you are using is not up to the task. Try downloading Packet Tracer, that is a good sim to start with.